Local Security Authority Protection (LSASS) is a critical component of the Windows operating system responsible for enforcing security policies, validating user logins, and managing security tokens. However, when LSASS protection is off or compromised, it can leave your system vulnerable to various security threats, including malware attacks, data breaches, and unauthorized access. In this comprehensive guide, we’ll delve into the significance of LSASS protection, common vulnerabilities, and strategies to ensure its security.
What is Local Security Authority Protection (LSASS)?
Local Security Authority Protection (LSASS) is a process in Windows operating systems responsible for authenticating users, enforcing security policies, and generating access tokens. It plays a crucial role in maintaining the overall security and integrity of the system by managing user logins, validating credentials, and controlling access to resources.
Importance of LSASS Protection:

- Prevention of Credential Theft: LSASS protection helps prevent credential theft by safeguarding sensitive information such as user passwords and authentication tokens.
- Mitigation of Malware Attacks: Malware often targets LSASS vulnerabilities to gain unauthorized access to the system or extract sensitive data. Enabling LSASS protection can mitigate the risk of such attacks.
- Enhanced System Security: By ensuring the integrity of the LSASS process, overall system security is enhanced, reducing the likelihood of security breaches and unauthorized access.
- Compliance Requirements: Many regulatory frameworks and industry standards, such as GDPR and PCI DSS, mandate the implementation of robust security measures, including LSASS protection, to safeguard sensitive data and ensure compliance.
Common LSASS Vulnerabilities:
- Memory Scraping Attacks: Attackers exploit vulnerabilities in LSASS to scrape memory for sensitive information, such as passwords and authentication tokens, allowing them to gain unauthorized access to the system.
- DLL Injection: DLL injection attacks involve injecting malicious code into the LSASS process, enabling attackers to execute arbitrary commands, steal credentials, or escalate privileges.
- Pass-the-Hash Attacks: Pass-the-Hash attacks involve using hashed credentials obtained from LSASS memory to authenticate and gain access to other systems within the network.
- Brute Force Attacks: Attackers may attempt to brute force login credentials by repeatedly guessing passwords, exploiting weak authentication mechanisms, or leveraging leaked credentials.
Strategies to Secure LSASS:
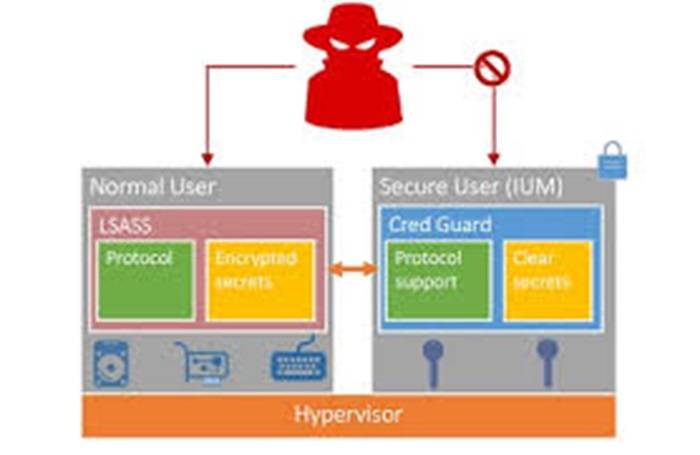
- Enable LSASS Protection Features: Windows operating systems offer various features and security mechanisms to protect LSASS, such as Credential Guard, Protected Process Light (PPL), and Virtualization-based Security (VBS). Ensure these features are enabled and properly configured to enhance LSASS security.
- Implement Strong Password Policies: Enforce strong password policies to prevent unauthorized access and mitigate the risk of brute force attacks. Encourage users to use complex passwords and implement multi-factor authentication (MFA) where possible.
- Regular Software Updates: Keep your operating system and security software up to date with the latest patches and updates to address known vulnerabilities and mitigate the risk of exploitation.
- Monitor LSASS Activity: Implement robust logging and monitoring solutions to track LSASS activity and detect any suspicious behavior or unauthorized access attempts promptly.
- Limit User Privileges: Follow the principle of least privilege and ensure users only have access to the resources and privileges necessary to perform their job responsibilities. Restrict administrative privileges to authorized personnel only.
- Educate Users about Security Best Practices: Train employees on security best practices, such as avoiding suspicious links and email attachments, using secure passwords, and being vigilant against social engineering attacks.
Local Security Authority Protection (LSASS) is a critical component of the Windows operating system that plays a vital role in enforcing security policies, validating user logins, and managing security tokens. Ensuring the security of LSASS is essential to mitigate the risk of malware attacks, data breaches, and unauthorized access. By understanding the importance of LSASS protection and implementing robust security measures, organizations can enhance their overall system security and safeguard sensitive information effectively. Remember, protecting LSASS is not just a recommendation but a necessity in today’s threat landscape.


